Existing users: login with WebID
On the first screen of My Move, we checked whether the user already has a WebID. In case he or she does, My Move should make sure the user can get logged in.
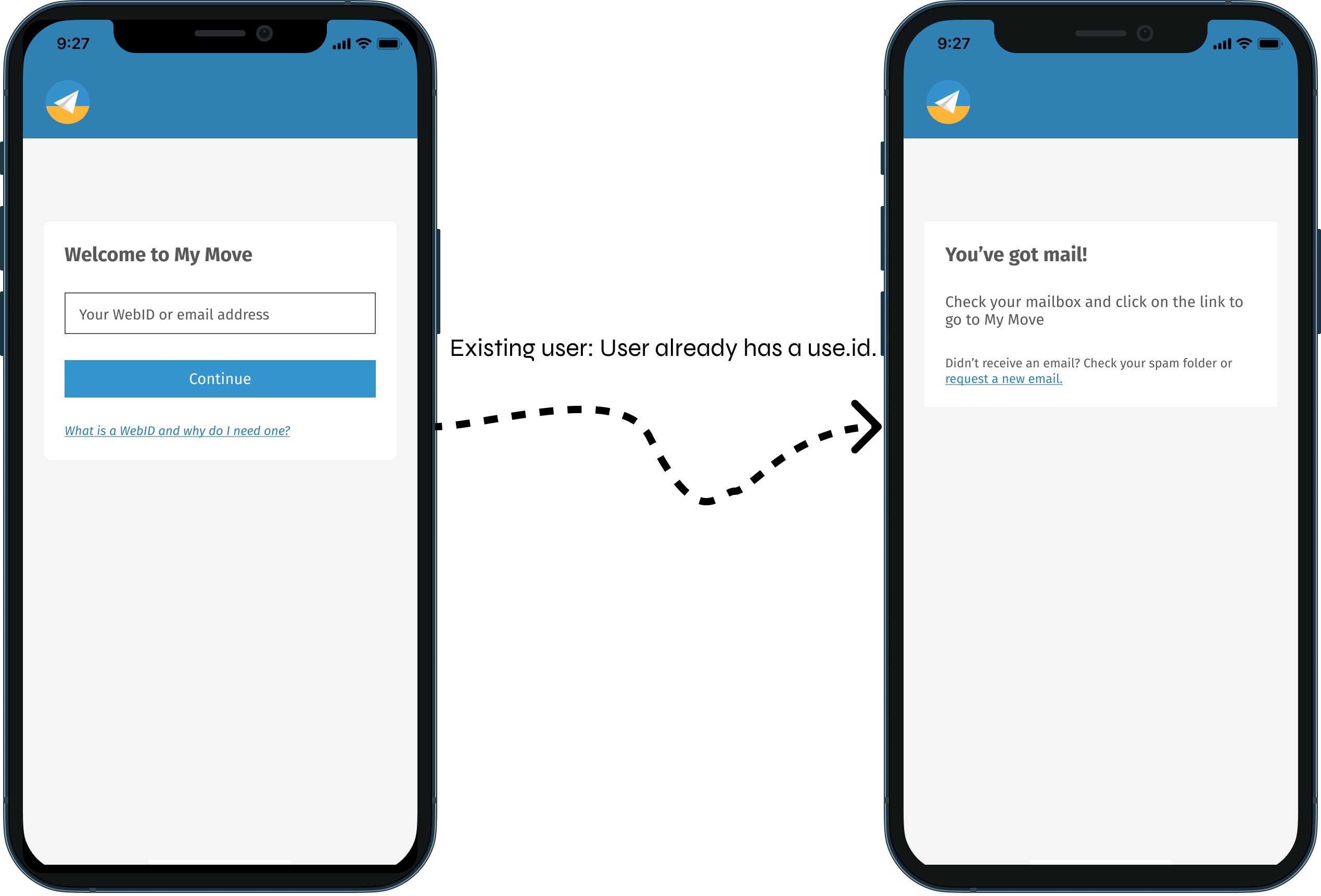
An existing user already has a WebID this WebID could be a use.id WebID or not.
For existing users (i.e. users with a WebID), there are two scenarios:
- Scenario 1: The user has a use.id WebID
In this case there are two subscenarios regarding on what he or she entered in the input field on the first screen:- The user has entered his or her use.id WebID
In this case, My Move has the option to use the use.id IDP in two ways: the app can either make use of the Solid OIDC flow or the/passwordless/email/sendendpoint. My Move chooses to use the latter because it eliminated several steps in the user journey. - The user has entered his or her use.id email address
In this case, My Move has to use the/passwordless/email/sendendpoint because it is the only way to let a user login based on his or her email address (unless My Move uses the/account/existsendpoint to figure out the user's WebID).
- The user has entered his or her use.id WebID
- Scenario 2: The user has a WebID other than a use.id
In this case, My Move must make use of the Solid OIDC flow. However, My Move currently decides not to support this journey because of the reasons outlined in User onboarding at My Move
use.id specific functionality
This guide only considers the
/passwordless/email/sendendpoint, which is proprietary to use.id. An alternative to this endpoint would be to use the Solid OIDC flow, which is part of the Solid standard. To learn how Solid OIDC would work with My Move (or any other app), please check the Solid OIDC and My Move guide.
My Move and the passwordless journey (non Solid OIDC)
In the following steps you can see how the My Move developers used the /passwordless/email/sendendpoint to let John log in. This endpoint allows the developers to skip the first few steps in the OAuth2 Code Grant Flow.
Step 1: Send an email to John containing a magic link to login
First, the developers send the following request to the use.id identity provider.
POST https://sandbox.idp.use.id/passwordless/email/send/passwordless/email/send
Content-Type: application/json
{
"selector":"email",
"email":"[email protected]",
"redirect_uri":"https://app.mymove.app/redirect",
"state":"789"
}
Now, an email has been sent to [email protected] containing a magic link. Once John clicks on that link, he will be redirected to the redirect URI that was specified in the previous request. This redirect URI will contain the code and the stateas a query parameter. In this case, the request URI looks as follows:
https://app.mymove.app/redirect?code=g0ZGZmNjVmOWIjNTk2NTk4ZTYyZGI3&state=789
Now that we have the authorization code, we can exchange it for an access token and an identity token in Step 3.
Step 2: Get the location of the client-id.jsonld document
Starting from this step, the My Move developers can switch back to the Solid OIDC flow. In Solid OIDC, dynamic client registration is a bit different. That is, each application that wants to support Solid, needs to have a client-id document. This document contains information about the application that would otherwise be registered at the IDP using dynamic client registration.
In use.id, by convention, this document is stored in the root of the pod of the application.
How to get the client-iddocument of My Move? Well, just surf to My Move's WebID and check the value of pim:storage and put /client-id.jsonld next to it.
For use.id, this becomes <https://sandbox.pods.use.id/f854f575-3c41-5466-83c2-794541f5a0ac/client-id.jsonld>.
It is important that the
redirect_urithat is used in the login requests in this guide matches one of theredirect_uriin theclient-iddocument.
Step 3: Exchange the authorization code for an access and identity token
The My Move developers now can use the token endpoint to exchange John's authorization code for a token. To do this, they send the following request:
POST https://sandbox.idp.use.id/oauth/token
DPoP eyJhbGciOiJSUzI1NiIsInR5cCI6ImRwb3Arand0IiwiandrIjp7Imt0eSI6IlJTQSIsImUiOiJBUUFCIiwidXNlIjoic2lnIiwia2lkIjoibEpkVS9hU2l1RnpPVkJNY0RRYnBpVHJjSXZNPSIsImFsZyI6IlJTMjU2IiwibiI6InNhMkptYW44WV8wbWlFdUtNYnBiRzE5bThRZ3BqNGxNbE9SM1RZb3JSSEwyelZhdV9LczNYQzdYcXhFY2FxUlhQeUhmYkotYlo3RlpwX1Z1dGJveTd4SjdGVGx3RGtGZ2EtWWRqdHBPZnR0ZGtFZ1pSNm16cXVuNzJsNEdiMzRlbmJHNTRVbGRVU0o0SUROUXEyWG9VMHpLc0tpREFpTjQxN1dkd04yb2UxbjFPSzh3STktMS1qOGhQVzVyamR0aVd4djBZMFVhVXFaZnBqVWsyLURfMHJrZVhDQ3BYeUJqX1EtR2JvNVVxS2k1TjdpeDY0c1VQVXlSOXZsZnJkOGdRV1pQVU5UdlFhVXJkQ2NNanhQdHZvYzNUcjgzUEdXMlJ4cFRnaUhPX1FDeWxXNm5TMG1hUWJFMGNVVU5PQlBsanhGZGN3b3dqSXJUamFFMnloVTg5dyJ9fQ.eyJodG0iOiJQT1NUIiwiaHR1IjoiaHR0cHM6Ly9zYW5kYm94LmlkcC51c2UuaWQvb2F1dGgvdG9rZW4iLCJqdGkiOiJiYjJhY2QwOC04MWE2LTRmZjctYjU5NS1iOWQ2ZGE3MTJmY2MiLCJpYXQiOjE2NjE1MTgxMzZ9.UKqe0jK2B0_4k3E1tBrBobzq9i2pvKY9xPQowGAs4mbiLRcRsXbBLNLInybtDHfwRDk74EOrJpqV0jy962C4uQ0sgBgQ6R3CARa1_-bHwTyL3BUtnSh1DIn4Dtbsg5AtTZt4KkCFFew4n1TBZFwo0LwHgIT_ORlmsc-pxfyQZNA9YgfvTgOakRFdn3OJJ_b_YDCGi3dRzEavrQasLyna3P9k-iRq0NZO4cPQ_A4E5VcLf2L4XhgDYiJcaS_BpS2c09PZR52oBssnkgcZ588vDIXR87AJ5FYCeRBd9_JA4e3Bea5AdnXDwlGp7iGAv1dN40Hv8Nz8G4qlnPJVL6opHA
Content-Type: application/x-www-form-urlencoded
grant_type=authorization_code
&code=g0ZGZmNjVmOWIjNTk2NTk4ZTYyZGI3
&redirect_uri=https://app.mymove.app/redirect
&client_id=https://sandbox.pods.use.id/f854f575-3c41-5466-83c2-794541f5a0ac/client-id.jsonld
After the developers have sent this request, they get the following response:
HTTP/1.1 200 OK
Content-Type: application/json
{
"access_token": "eyJhbGciOiJFUzI1NiIsImtpZCI6ImQ3NGMxZGZlLTFhNDEtNGEyMC1hNDJkLWZmYzBmMmJkZGE5OCIsInR5cCI6ImF0K2p3dCJ9.eyJzdWIiOiJlbWFpbHw2MzA4YzEwMmMzN2RlMzViZGVkZTI3NGUiLCJhdWQiOlsidERVT0l2WWo1bFZLUTJNUWtFYXFjU1J6ZkhleUljVGciLCJzb2xpZCJdLCJpYXQiOjE2NjE1MTgxNDcsImV4cCI6MTY2MTU1NDE0NywiY2xpZW50X2lkIjoiaHR0cHM6Ly9zYW5kYm94LnBvZHMudXNlLmlkL2Y4NTRmNTc1LTNjNDEtNTQ2Ni04M2MyLTc5NDU0MWY1YTBhYy9jbGllbnQtaWQuanNvbmxkIiwiY25mIjp7ImprdCI6IjdYQW1OYy11Mk92SDc3bE9SUlV3Y1ZNcVh6dFlGUDZSamdmTDNfUnpXUXcifSwid2ViaWQiOiJodHRwczovL3NhbmRib3gudXNlLmlkL3Rlc3RfMjAyMl8wOF8yNl8xNF80N181MyIsImp0aSI6IjJiMmZiMjViLTgzMzctNGQ0Mi05ZTFlLTRjMDJkYTdhMjBkZiIsImlzcyI6Imh0dHBzOi8vc2FuZGJveC5pZHAudXNlLmlkLyJ9.uGXL3o-FCciyLHkDaSypINb4lq116fT7PQsNxh_LcZ6yam11FHLsKLX-640rAkBuGRwBxkWmhSpkBpIwR1ssFQ",
"id_token": "eyJhbGciOiJFUzI1NiIsImtpZCI6ImQ3NGMxZGZlLTFhNDEtNGEyMC1hNDJkLWZmYzBmMmJkZGE5OCIsInR5cCI6IkpXVCJ9.eyJodHRwczovL3NhbmRib3gudXNlLmlkL3dlYmlkIjoiaHR0cHM6Ly9zYW5kYm94LnVzZS5pZC90ZXN0XzIwMjJfMDhfMjZfMTRfNDdfNTMiLCJpc3MiOiJodHRwczovL3NhbmRib3guaWRwLnVzZS5pZC8iLCJzdWIiOiJlbWFpbHw2MzA4YzEwMmMzN2RlMzViZGVkZTI3NGUiLCJhdWQiOiJodHRwczovL3NhbmRib3gucG9kcy51c2UuaWQvZjg1NGY1NzUtM2M0MS01NDY2LTgzYzItNzk0NTQxZjVhMGFjL2NsaWVudC1pZC5qc29ubGQiLCJpYXQiOjE2NjE1MTgxNDcsImV4cCI6MTY2MTU1NDE0Nywic2lkIjoidXlBMlpxZlJOQmR4SmsybUwwbF9JZ2dXSXg0SVdSX3MiLCJ3ZWJpZCI6Imh0dHBzOi8vc2FuZGJveC51c2UuaWQvdGVzdF8yMDIyXzA4XzI2XzE0XzQ3XzUzIiwianRpIjoiMDg0NWM0MGYtZDY5Ny00MzUyLWE4MWUtODRhNDgyYmE2YzIyIn0.WG3euzaPRU-3lv71NWkoXRV5mhFpF_WtATrywDF7a6L0JFs3GvwZSdqF8Ui9weOLNwJmnsAh_eSIQAFdYrb-5g",
"scope": "openid",
"expires_in": 86400,
"token_type": "DPoP"
}
Voila, you now have an access token and identity token for John. This means that John is now logged in to My Move!
Updated almost 2 years ago